
SharePoint Online’s support for sharing sites and documents with external users has been there a while now, but sharing with each individual users is quite cumbersome if you have to share with a volume of users. This is where Azure B2B comes into play, and the Azure team has good information on this over at Github.
Steps covered in this post:
- Create AAD security group
- Enable external sharing in a site collection
- Add AAD security group in the site’s Members group
- Create and upload CSV file with all external users to AAD
- Accept invitation and have bliss!
What is Azure B2B?
Azure B2B collaboration lets you enable access to your corporate applications from partner-managed identities. You can create cross-company relationships by inviting and authorizing users from partner companies to access your resources. Resources can be any Azure AD registered application in your tenant. Complexity is reduced because each company federates once with Azure Active Directory and each user is represented by a single Azure AD account. Security is increased because access is revoked when partner users are terminated from their organizations, and unintended access via membership in internal directories is prevented. For business partners who don't already have Azure AD, B2B collaboration has a streamlined sign-up experience to provide Azure AD accounts to your business partners.Note that as of today (April 28th, 2016) Azure B2B is still in public preview and has not made general availability yet. The samples they have does not match their own documentation 100% either :)
Benefit of Azure B2B with SharePoint Online
Instead of inviting external users one by one to a site collection in SharePoint Online, you can add them via an AAD security group instead which again is added to a SharePoint group at the site itself, much like you would do for on-premises SharePoint. And you invite them in a controlled manner – which may seem harder to the individual user though ;) But we’re all IT Pro’s here right? It’s also quicker to add the AAD security group to multiple sites compared to inviting users over and over.There are some other posts out there on the interwebs on this topic, but due to samples and documentation being in flux in this preview I decided to write it up. I’ll list issues I encountered with the other samples in the reference section at the end of this post.
Step 1 – Create AAD security group
 Log into the Office 365 tenant you want to invite the external party to as a tenant admin. From the tenant admin page click Azure AD. If you have signed up for the Azure subscription associated with your tenant this will take you to the Azure management portal. If not you need to sign up or figure out how to do all the steps via AAD PowerShell instead.
Log into the Office 365 tenant you want to invite the external party to as a tenant admin. From the tenant admin page click Azure AD. If you have signed up for the Azure subscription associated with your tenant this will take you to the Azure management portal. If not you need to sign up or figure out how to do all the steps via AAD PowerShell instead.Signing up to Azure is however free as long as you’re not using any of the paid services.

In the Azure management portal (the old one) enter the settings for the AAD, click Groups and Add a group.

Next you want to store the GUID of the security group. You can either get this via AAD PowerShell or copy it from the browser URL of the group itself which is much quicker.
https://manage.windowsazure.com/contoso.onmicrosoft.com#Workspaces/ActiveDirectoryExtension/Directory/fc4d56df-dd58-4aea-9e4e-3b6852fbc365/Group/35fca7da-b67a-43d6-91bd-4786f2b83825/groupMembers
Step 2 – Enable external sharing on a site collection
In the SharePoint Online admin center I created a new site collection named B2B. Next I enabled external sharing requiring users to be authenticated. If you don’t allow sharing your external users won’t be able to access the site.
Step 3 – Add AAD security group to the sites Members group
I want my external users to have contributor rights in my site, so the next step is adding the AAD security group, Puzzlepart External, from step 1 to the site’s Members security group.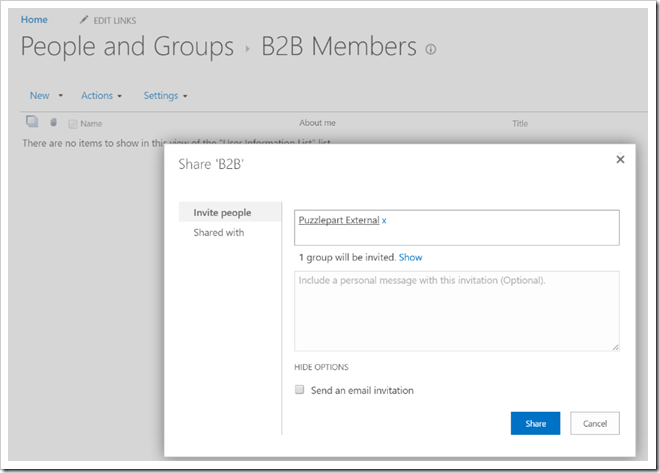
Step 4 – Create and upload CSV file with external users
In order to add and invite the external users you have to create a CSV file with one row per user you want to invite. The below sample will add one user. Row one has the headers, and the following rows data per user.Email,DisplayName,InvitationText,InviteRedirectUrl,InviteAppID,InviteGroupResources mikael.svenson@fabrikam.com,Mikael Svenson,<p>Welcome Mikael Svenson!</p>,https://contoso.sharepoint.com/sites/b2b,00000003-0000-0ff1-ce00-000000000000,35fca7da-b67a-43d6-91bd-4786f2b83825
- Email – address and login for the external user
- DisplayName – Name to be populated in Azure AAD for the user
- InvitationText – custom text in HTML for the invitaion e-mail (optional)
- InviteRedirectUrl – URL where we want to send the user after accepting the invitation, in my case the B2B SharePoint site (optional)
- InviteAppID – App principal id for SharePoint Online. This is 00000003-0000-0ff1-ce00-000000000000 for all tenants (not 100% sure if needed)
- InviteGroupResources – GUID of the AAD security group(s) you want the user added to. (space delimited if more than one)
If all goes according to plan the status page should show something like this.

Step 5 – Accept the sharing invitation and start collaborating
The invited user will receive an invitation e-mail with a link to accept the invitation.
Clicking the link takes you to a page where it prompts you to sign in with account which received the e-mail, which means you cannot just forward it to someone else.

Clicking Next will either sign you in automatically if you have signed in to Office 365 already, or it will take you to the sign in page. Next it should re-direct you to the shared site specified in the CSV file. You might get an access denied the first time as it takes a few seconds for the user to be properly added to AAD, but if you refresh the page you should get access.
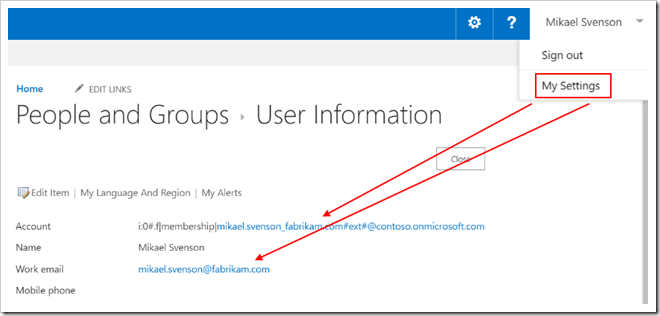
Here’s the data displayed for the external users settings page once logged in to the B2B site.
Tips
It might be a good idea to post-fix something to the display name of the external user to more easily identify an external user. Something like- Mikael Svenson (external)
- Mikael Svenson (Puzzlepart)
References
Steve Peschka’s Azure B2B First Look post from September 2015 does a good job at explaining how it all works and has a sample CSV file. It uses a GUID to an application in the InviteAppID which I’m not sure what is. In my case I used the GUI for SharePoint, but not sure if it’s needed at all.Arjan Corenelissen has a post from April 2016 which references a post for the CSV file at https://azure.microsoft.com/en-us/documentation/articles/active-directory-b2b-references-csv-file-format/ (March 2016). Here it says to set the InvitedToApplications attribute the the SharePoint GUID. If I add InvitedToApplications to my CSV file the import fails every time. Seems using the InviteAppID works better.
The Azure team also has a CSV reference at Github which also has fields not working – which seems to be the same doc as on azure.microsoft.com.
